Flare-On 2024 (1 of 10)

If you want to flex your Reverse Engineering skills, try solving challenges at Flare-On. This is their 10th annual edition of 2024.
Challenge 1: X
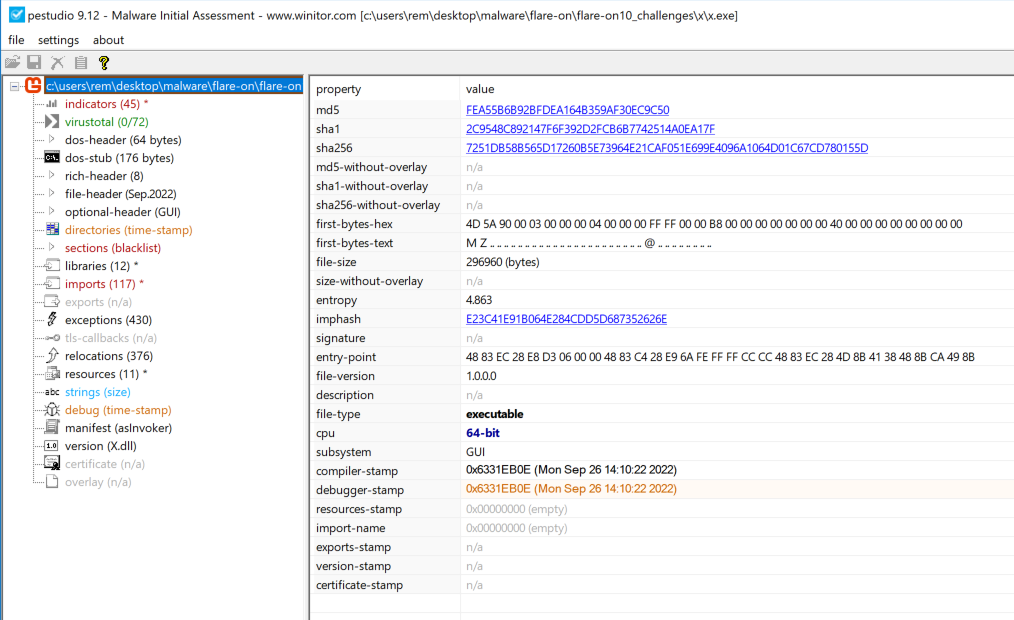
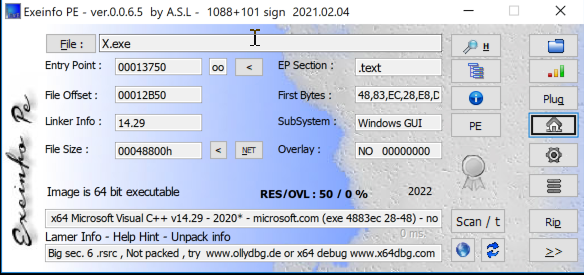
Flare-On always gets you hooked into the CTF by teasing you with a simple first challenge. We are provided with a zip file called X and on extraction you can see an executable and some dll files. You can make an assumption that this could be a windows executable but check to make sure. I always get started with some static analysis. I used PEStudio and EXEInfo and dragged the X.exe into the tool to get a closer look.
Summary
- It is a x64 Microsoft Visual C++ v14.29 - 2020. It has a Windows GUI
- Strings: Nothing crazy going on here, I see a lot of readable strings, it is probably not packed.
- Imports: I see IsDebuggerPresent which is worth making a note of. This import might not allow you to run it properly in a debugger. It also has other imports related to 'api-ms-win-crt-*.dll' which is probably facilitating C / C++ runtime.
- Version: The OriginalFileName is X.dll which doesn't reveal much yet but worth investigating if the X.exe file does not give you any meaningful results.
- Next Options?: Run the executable in a safe and controlled lab environment and maybe take a look at it in a debugger (dead end).

Since this is a CTF, I will make an assumption that the correct value will provide me with a flag. However, this could also be a trojan horse, i.e. something else might be happening while you fool around with this silly game 🤞
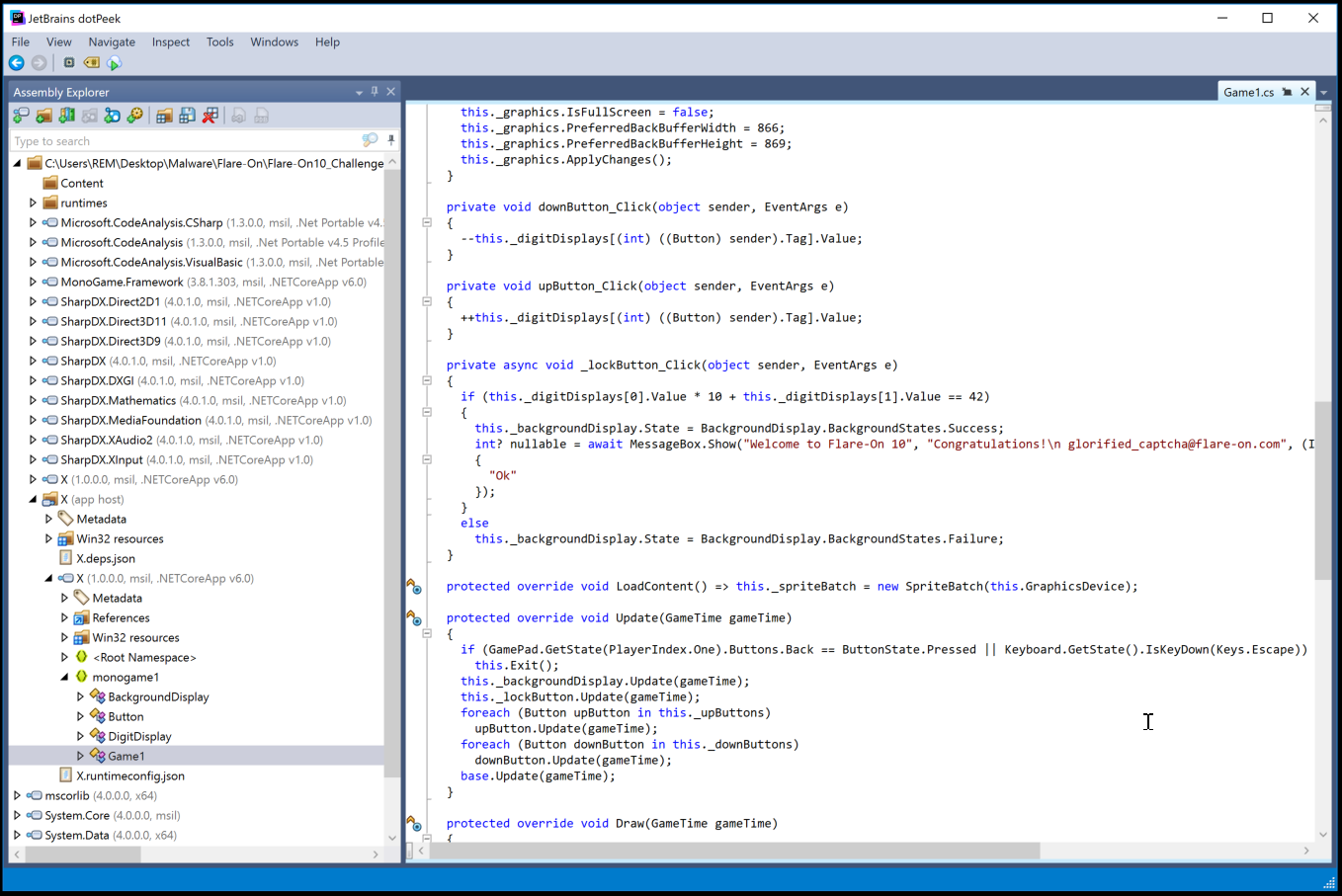
I have a feeling that you could easily decompile this using your favorite decompiler, I loaded this up in 'Ghidra' as I already have it setup in my lab environment. I also had a sense that I could use a tool more suitable for these type of binaries such as ILSpy or dotPeek which could directly provide me the source code vs looking at the semi-source code in 'Ghidra'. I decided to open the X folder on dotPeek by JetBrains.
Summary
- I am using dotPeek for the first time but the interface is similar to other .NET decompilers. When you load the X folder, you see a lot of standard Microsoft libraries used by your application and in this case a clearly labeled section of X. Many of the times this information is stripped out which makes it more difficult to analyze but the symbol information is still intact in this case.
- The two best options now are to look for a) A hardcoded conditional statement for the two digits (input) or b) look at the code for what happens when you click the lock button (output) to validate your answer and toggle the conditional check for your answer in a debugger.
- The lockButton_Click function of the Game1 section reveals the conditional statement. It looks for the magical number '42'. In this case (10 * 4 + 2)
Solution:

